Note: links in this article have been verified to be secure
Cyber criminals often look to capitalize on the confusion surrounding national events and crises, so the past couple years have pretty much been their dream come true.
According to the FBI, phishing was the most common type of cybercrime in 2021—and phishing incidents rose by 34 percent, from 241,324 incidents in 2020, to 323,972 incidents in 2021—resulting in over $44 million in total victim loss. So, why do the number of data breaches—specifically in regards to phishing scams—continue to rise each year? According to Verizon's 2022 Data Breach Investigations Report (DBIR), 82 percent of data breaches involve some sort of human or user-driven element, including falling for a phishing scam and providing your information to an untrustworthy source. Thankfully, many of these breaches can be avoided by understanding the common warning signs of a phishing message.
About 96% of phishing attacks arrive by email. Another 3% are carried out through malicious websites and just 1% via phone. The increase in phishing attacks means email communications networks are now riddled with cybercrime. Symantec research suggests that as recently as 2020, 1 in every 4,200 emails was a phishing email.
While all major email providers have security measures in place to prevent suspected phishing emails, cyber criminals continue to find new ways to disguise their intentions and slip through the cracks. As a result, common sense and a trained eye are still the best defenses against falling victim to a phishing scam.
Here’s are some common warning signs to look for if you suspect a phishing email:
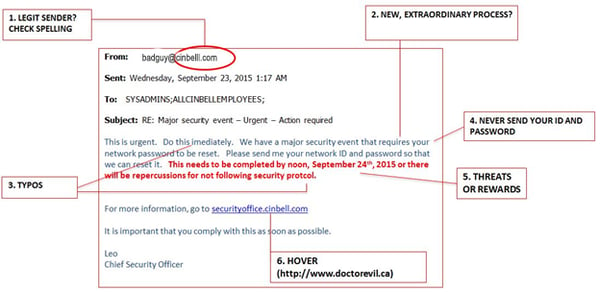
- The sender's email address
Cyber criminals take drastic measures to make their emails look legitimate. They know one of the first things a recipient looks at when opening an email is who it's from so they try to replicate familiar addresses. Often these addresses include a slight misspelling that can be overlooked if you don't pay close attention. - It asks you to do something that seems out of the ordinary
Trust your gut. If an email is asking you to do something that seems out of the ordinary, treat the message as suspicious. Confirm with the source that the message is legitimate before clicking on any links or responding with personal information. - Contains typos
Many phishing attempts originate from foreign hackers for whom English is a second language. As a result, many phishing emails contain typos, misspellings and clumsy wording. - Asks for login credentials or personal information
No reputable company will ever send you an email asking you for your password, credit card number, bank account information, or other personal information. A request to send this type of information via email is a strong sign of a phishing attempt. - Makes a threat or promises extraordinary rewards
Cyber criminals want you to react to their emails quickly before you have time to recognize the red flags. They will often include an element of urgency or consequence in their messages to motivate you to respond quickly and distract you from considering its legitimacy. - Contains masked links
The goal of many phishing emails is to get you to click on a link that will begin the installation of malware on your computer. If you ever have concerns about the legitimacy of an email, you can place your cursor over any hyperlinked text to see exactly what URL it will open. If the URL that is shown does not appear to fit with the hyperlinked text, it is likely a phishing scam.
Legitimate senders: just when you thought you were getting good at spotting phishing…
A disturbing trend in phishing scams is the use of legitimate senders in e-mail messages. This can happen when a person who you may have already exchanged legitimate e-mails with has had their account hijacked by cyber-criminals. Since the cyber-criminals have access to a live email account, they can make phishing e-mails look quite authentic, even mimicking the writing style of the compromised account holder.
You can still use some of the techniques above to help set off your “scam-meter”, especially if you are being asked to do something that doesn’t feel right. Note, however, that phishing-emails from legitimate senders can appear personable and convincing.
What to do if you receive a suspected phishing attempt
If you receive an email you believe to be a phishing attempt, here’s what you should and shouldn’t do:
- DO NOT click any links or attachments, or provide the sender with any information as the security of your hardware and information could be compromised.
- Mark the email as spam. If you are using the Cincinnati Bell/altafiber web-based email client (webmail2.cincinnatibell.net), you can click the Spam button that is available at the top of the screen. If you are using a mobile device, or another email client, select “Report as spam/junk” (or similarly named option). This will remove the email from your inbox and enable us to better identify and filter spam messages in the future.
If you responded to a suspected phishing email and believe your personal information (login credentials, Social Security number, financial information) has been compromised, or if you have clicked the link and/or already provided any information, you should scan your device for malware using your anti-virus/malware program. If you don't have anti-virus/malware program, see the section below about altafiber's Premier Internet offering. Also, change the passwords for any accounts you have logged into since clicking the link. Then, visit IdentityTheft.gov to see what steps you should take depending on what information may have been exposed.
Additional tips to consider
Limit the reuse of passwords - Scammers will reuse passwords they compromise or obtain through the dark web to attempt additional fraud or data theft. You should pick a strong password for your altafiber email account and not reuse it on other websites. Strong passwords should be at least 8 characters and contain upper and lower case alphabetic characters, numbers and special characters.
Ensure your mobile device is using e-mail encryption – To ensure your altafiber email account is secure on your mobile device make sure encryption is enabled. You can easily enable encryption on your mobile device by checking the server settings in your mobile email client. If no security type or option is selected, enable TLS (accept all certificates).